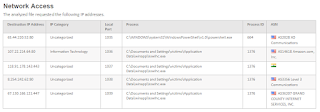
Yes... we know the famous James Bond movie was titled, "From Russia with Love", however, in this case we're going to Russia. What? Well.... as previously noted here, the botnet owners are starting to phone home via encrypted channels. We have a similar situation this afternoon with Russia, specifically Moscow, being the destination. Let's follow the bouncing ball:
An M$ Word file is propagating the Internet currently that drops 27 files and launches Powershell:
Many connections are initiated outbound, mostly on TCP Port 80, but... notice the TCP:443 connection back to Mother Russia:
How many AV Engines are currently protecting against this threat you ask? Not good... only 7 of 58:
Final question - are you decrypting outbound HTTPS connections? Further, are you interrogating the outbound Posts for DLP Violations? Call ESPO Systems if you need help...
ESPOSystems
Thursday, August 31, 2017
Monday, July 3, 2017
Phone Home via HTTPS/TCP:443
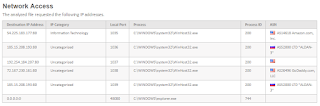
It's happening! The malware authors are transitioning from HTTP to HTTPS as the callback mechanism to their Botnets. Per this Forcepoint Sandbox Report, you'll see that a Microsoft Word File w/bad macro is propagating today with a very low catch rate... unfortunately only 6 out of 56 Security Companies are currently detecting this as malicious:
Again, per the report above, note how the malware is phoning back home to India via TCP Port 443:
How do we know this server is Command-and-Control for a botnet... via Forcepoint's ThreatSeeker Database:
In summary, this begs a question - are you decrypting your HTTPS traffic? If not, consult with an ESPO Systems expert to discuss Best Practices.
Again, per the report above, note how the malware is phoning back home to India via TCP Port 443:
How do we know this server is Command-and-Control for a botnet... via Forcepoint's ThreatSeeker Database:
In summary, this begs a question - are you decrypting your HTTPS traffic? If not, consult with an ESPO Systems expert to discuss Best Practices.
Tuesday, May 16, 2017
WannaCry Defense
After several days there is still much speculation regarding how this Microsoft Vuln (CVE-2017-0145) is initially being exploited. This is due to the fact that the worm spreads via SMB so aggressively after infestation that it's hard to back track. However, per this report last night, most people are leaning towards inbound emails with attachments.
We at ESPO have been watching the Forcepoint Email Sandbox since Friday and agree. This morning is a perfect example. Emails are coming in with attachments referencing invoices:
As you'd expect, and our endusers unfortunately don't, it's socially engineered to pop open a Word Doc with Macro:
As we follow the bouncing ball you'll note that this blended threat then pulls the actual exploit via the web channel (still in the clear... not using https):
How are the AntiVirus/Next Gen Endpoint guys doing regarding detection rate? Ummm... not good (only 10 out of 57 companies currently detect it):
In summary, ping us at ESPO to discuss how a holistic security solution (Web, Email, Firewall/IPS, Patch Mgt and DLP) can preclude you from wasting time on this latest worm.
We at ESPO have been watching the Forcepoint Email Sandbox since Friday and agree. This morning is a perfect example. Emails are coming in with attachments referencing invoices:
As you'd expect, and our endusers unfortunately don't, it's socially engineered to pop open a Word Doc with Macro:
As we follow the bouncing ball you'll note that this blended threat then pulls the actual exploit via the web channel (still in the clear... not using https):
How are the AntiVirus/Next Gen Endpoint guys doing regarding detection rate? Ummm... not good (only 10 out of 57 companies currently detect it):
In summary, ping us at ESPO to discuss how a holistic security solution (Web, Email, Firewall/IPS, Patch Mgt and DLP) can preclude you from wasting time on this latest worm.
Wednesday, December 7, 2016
Keeping up with evolving cyber security needs
As VP of Worldwide Channel Sales and Operations at FireMon, Mr. Kurt Mills, via his years of building Top Tier Vendor Partner Programs, is uniquely positioned to identify effective Cyber Security strategies. After all... his resume highlights a who's who of the Security Industry:
Firemon
Websense / Forcepoint
Secure Computing / McAfee
Symantec / Bluecoat
8e6
TopLayer
F-Secure
What recommendation does Mr. Mills have to address the Cyber Security Skills shortage we find ourselves in... along with an increasingly sophisticated Threat Landscape? Partnering with Subject Matter Experts (SMEs) to ensure client networks are setup in such a way that the Security Controls are optimally deployed/tuned.
In summary, as we all know and as common sense dictates, if you don't use it... you lose it. Mr. Mills identifies a flexible education & partnering model in his ChannelPro article that will ensure we all meet the evolving Cyber Security needs of our clients by focusing on solutions within our sweet spot... and partnering on others.
Firemon
Websense / Forcepoint
Secure Computing / McAfee
Symantec / Bluecoat
8e6
TopLayer
F-Secure
What recommendation does Mr. Mills have to address the Cyber Security Skills shortage we find ourselves in... along with an increasingly sophisticated Threat Landscape? Partnering with Subject Matter Experts (SMEs) to ensure client networks are setup in such a way that the Security Controls are optimally deployed/tuned.
In summary, as we all know and as common sense dictates, if you don't use it... you lose it. Mr. Mills identifies a flexible education & partnering model in his ChannelPro article that will ensure we all meet the evolving Cyber Security needs of our clients by focusing on solutions within our sweet spot... and partnering on others.
Monday, October 24, 2016
Dirty Cow (CVE-2016-5195)
Beware - Dirty Cow is a local privilege escalation vuln just publicly announced. How bad is this? Very... this provides root access! Check out the following video for description:
Not good right? No worries... CentOS/Redhat will have a patch. Ummmm... not yet:
Thankfully, the ESPO Systems EU Team, led by Adrian Nykiel, has your back. He has built the bugfix into the ESPO Systems Forcepoint Virtual Proxy.
In summary, as seen above, ESPO is blessed to have many Security Studs on-board. Contact your Sales Pro to arrange for a free consultation.
Not good right? No worries... CentOS/Redhat will have a patch. Ummmm... not yet:
Thankfully, the ESPO Systems EU Team, led by Adrian Nykiel, has your back. He has built the bugfix into the ESPO Systems Forcepoint Virtual Proxy.
In summary, as seen above, ESPO is blessed to have many Security Studs on-board. Contact your Sales Pro to arrange for a free consultation.
Thursday, October 6, 2016
Malwarebytes... Really???
Remember when we were all throwing Malwarebytes onto the desktops? It was all the rage for a while. Seems as if that ship has sailed. Case in point:
- On Monday, October 3rd, a Microsoft Word document with malicious macro began propagating across the internet. Per this Forcepoint File Sandbox Report, the file is doing a number of malicious things... such as phoning home to Mother Russia:
- Within a few hours the AV coverage rate, as seen via VirusTotal, was only up to 3 of 54 "solutions":
- What is the coverage rate this morning you may ask? A full 3 days later? Only 31 of 54. Guess who is still AWOL:
In summary, Behavioral Analysis is the only way to address this onslaught of malware attacks. Call ESPO Systems for a free consultation regarding which solutions are performing best in the real world.
- On Monday, October 3rd, a Microsoft Word document with malicious macro began propagating across the internet. Per this Forcepoint File Sandbox Report, the file is doing a number of malicious things... such as phoning home to Mother Russia:
- Within a few hours the AV coverage rate, as seen via VirusTotal, was only up to 3 of 54 "solutions":
- What is the coverage rate this morning you may ask? A full 3 days later? Only 31 of 54. Guess who is still AWOL:
In summary, Behavioral Analysis is the only way to address this onslaught of malware attacks. Call ESPO Systems for a free consultation regarding which solutions are performing best in the real world.
Monday, September 19, 2016
The Death of Commercial AV Products - Part Deux
There was a Microsoft Word file with a Malicious Macro being distributed via email this morning. AV Detection Rate was at the time very low for Stage 1 of this attack:
Thankfully, our Forcepoint(r) Sandbox is detecting it for us through a number of indicators, one of which shows a similarity to Zeus:
What else is happening in the attack? As usual it is Posting/Phoning home to Mother Russia along with an HTTP Get which downloads a .exe file:
What is the detection rate for this 2nd stage of the attack? Not so great either:
NOTE - did you see that CrowdStrike, with much fanfare, decided to contribute back to the Security Community by having their "Machine Learning" powered results displayed via VirusTotal? While it is good that, unlike many traditional signature based engines, CrowdStrike detected this threat in Stage 2. However, where was CrodStrike on Stage 1? No where on Virus Total can you find their results for that initial Word Doc. Are there agreements in place to only display their name when a positive detection is made? Seems fishy to us.
In any case, let us help you save money by installing next gen security solutions as the AV Vendors have once again proven unsuccessful. Call ESPO Systems if you need help... :-)
Thankfully, our Forcepoint(r) Sandbox is detecting it for us through a number of indicators, one of which shows a similarity to Zeus:
What else is happening in the attack? As usual it is Posting/Phoning home to Mother Russia along with an HTTP Get which downloads a .exe file:
What is the detection rate for this 2nd stage of the attack? Not so great either:
NOTE - did you see that CrowdStrike, with much fanfare, decided to contribute back to the Security Community by having their "Machine Learning" powered results displayed via VirusTotal? While it is good that, unlike many traditional signature based engines, CrowdStrike detected this threat in Stage 2. However, where was CrodStrike on Stage 1? No where on Virus Total can you find their results for that initial Word Doc. Are there agreements in place to only display their name when a positive detection is made? Seems fishy to us.
In any case, let us help you save money by installing next gen security solutions as the AV Vendors have once again proven unsuccessful. Call ESPO Systems if you need help... :-)
Subscribe to:
Comments (Atom)