It's happening! The malware authors are transitioning from HTTP to HTTPS as the callback mechanism to their Botnets. Per this Forcepoint Sandbox Report, you'll see that a Microsoft Word File w/bad macro is propagating today with a very low catch rate... unfortunately only 6 out of 56 Security Companies are currently detecting this as malicious:
Again, per the report above, note how the malware is phoning back home to India via TCP Port 443:
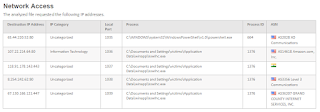
How do we know this server is Command-and-Control for a botnet... via Forcepoint's ThreatSeeker Database:
In summary, this begs a question - are you decrypting your HTTPS traffic? If not, consult with an ESPO Systems expert to discuss Best Practices.