As VP of Worldwide Channel Sales and Operations at FireMon, Mr. Kurt Mills, via his years of building Top Tier Vendor Partner Programs, is uniquely positioned to identify effective Cyber Security strategies. After all... his resume highlights a who's who of the Security Industry:
Firemon
Websense / Forcepoint
Secure Computing / McAfee
Symantec / Bluecoat
8e6
TopLayer
F-Secure
What recommendation does Mr. Mills have to address the Cyber Security Skills shortage we find ourselves in... along with an increasingly sophisticated Threat Landscape? Partnering with Subject Matter Experts (SMEs) to ensure client networks are setup in such a way that the Security Controls are optimally deployed/tuned.
In summary, as we all know and as common sense dictates, if you don't use it... you lose it. Mr. Mills identifies a flexible education & partnering model in his ChannelPro article that will ensure we all meet the evolving Cyber Security needs of our clients by focusing on solutions within our sweet spot... and partnering on others.
Wednesday, December 7, 2016
Monday, October 24, 2016
Dirty Cow (CVE-2016-5195)
Beware - Dirty Cow is a local privilege escalation vuln just publicly announced. How bad is this? Very... this provides root access! Check out the following video for description:
Not good right? No worries... CentOS/Redhat will have a patch. Ummmm... not yet:
Thankfully, the ESPO Systems EU Team, led by Adrian Nykiel, has your back. He has built the bugfix into the ESPO Systems Forcepoint Virtual Proxy.
In summary, as seen above, ESPO is blessed to have many Security Studs on-board. Contact your Sales Pro to arrange for a free consultation.
Not good right? No worries... CentOS/Redhat will have a patch. Ummmm... not yet:
Thankfully, the ESPO Systems EU Team, led by Adrian Nykiel, has your back. He has built the bugfix into the ESPO Systems Forcepoint Virtual Proxy.
In summary, as seen above, ESPO is blessed to have many Security Studs on-board. Contact your Sales Pro to arrange for a free consultation.
Thursday, October 6, 2016
Malwarebytes... Really???
Remember when we were all throwing Malwarebytes onto the desktops? It was all the rage for a while. Seems as if that ship has sailed. Case in point:
- On Monday, October 3rd, a Microsoft Word document with malicious macro began propagating across the internet. Per this Forcepoint File Sandbox Report, the file is doing a number of malicious things... such as phoning home to Mother Russia:
- Within a few hours the AV coverage rate, as seen via VirusTotal, was only up to 3 of 54 "solutions":
- What is the coverage rate this morning you may ask? A full 3 days later? Only 31 of 54. Guess who is still AWOL:
In summary, Behavioral Analysis is the only way to address this onslaught of malware attacks. Call ESPO Systems for a free consultation regarding which solutions are performing best in the real world.
- On Monday, October 3rd, a Microsoft Word document with malicious macro began propagating across the internet. Per this Forcepoint File Sandbox Report, the file is doing a number of malicious things... such as phoning home to Mother Russia:
- Within a few hours the AV coverage rate, as seen via VirusTotal, was only up to 3 of 54 "solutions":
- What is the coverage rate this morning you may ask? A full 3 days later? Only 31 of 54. Guess who is still AWOL:
In summary, Behavioral Analysis is the only way to address this onslaught of malware attacks. Call ESPO Systems for a free consultation regarding which solutions are performing best in the real world.
Monday, September 19, 2016
The Death of Commercial AV Products - Part Deux
There was a Microsoft Word file with a Malicious Macro being distributed via email this morning. AV Detection Rate was at the time very low for Stage 1 of this attack:
Thankfully, our Forcepoint(r) Sandbox is detecting it for us through a number of indicators, one of which shows a similarity to Zeus:
What else is happening in the attack? As usual it is Posting/Phoning home to Mother Russia along with an HTTP Get which downloads a .exe file:
What is the detection rate for this 2nd stage of the attack? Not so great either:
NOTE - did you see that CrowdStrike, with much fanfare, decided to contribute back to the Security Community by having their "Machine Learning" powered results displayed via VirusTotal? While it is good that, unlike many traditional signature based engines, CrowdStrike detected this threat in Stage 2. However, where was CrodStrike on Stage 1? No where on Virus Total can you find their results for that initial Word Doc. Are there agreements in place to only display their name when a positive detection is made? Seems fishy to us.
In any case, let us help you save money by installing next gen security solutions as the AV Vendors have once again proven unsuccessful. Call ESPO Systems if you need help... :-)
Thankfully, our Forcepoint(r) Sandbox is detecting it for us through a number of indicators, one of which shows a similarity to Zeus:
What else is happening in the attack? As usual it is Posting/Phoning home to Mother Russia along with an HTTP Get which downloads a .exe file:
What is the detection rate for this 2nd stage of the attack? Not so great either:
NOTE - did you see that CrowdStrike, with much fanfare, decided to contribute back to the Security Community by having their "Machine Learning" powered results displayed via VirusTotal? While it is good that, unlike many traditional signature based engines, CrowdStrike detected this threat in Stage 2. However, where was CrodStrike on Stage 1? No where on Virus Total can you find their results for that initial Word Doc. Are there agreements in place to only display their name when a positive detection is made? Seems fishy to us.
In any case, let us help you save money by installing next gen security solutions as the AV Vendors have once again proven unsuccessful. Call ESPO Systems if you need help... :-)
Wednesday, August 17, 2016
The Death of Commercial AV Products
We keep beating the drums... reduce what is most likely the largest line item in your Security Expense Budget, Anti-Virus. Another data point to make our case:
1. Microsoft Word file propagating the Internet as of ~8amCDT was detected by our Forcepoint Sandbox:
2. Note the SHA-256 Hash in the above screen shot. Note the same hash below and how only 5 of 53 AV Engines are currently detecting this threat:
3. How bad is the malware? Per below, it attempts to "post" some of your data to a site in the Ukraine:
In summary, did you see that Freeware AV Engines are detecting this threat? Why is it you're paying all that money to the "enterprise class AV companies"? Again... reduce your spend and invest the savings in next gen solutions. Call ESPO Systems for a free consultation.
1. Microsoft Word file propagating the Internet as of ~8amCDT was detected by our Forcepoint Sandbox:
2. Note the SHA-256 Hash in the above screen shot. Note the same hash below and how only 5 of 53 AV Engines are currently detecting this threat:
3. How bad is the malware? Per below, it attempts to "post" some of your data to a site in the Ukraine:
In summary, did you see that Freeware AV Engines are detecting this threat? Why is it you're paying all that money to the "enterprise class AV companies"? Again... reduce your spend and invest the savings in next gen solutions. Call ESPO Systems for a free consultation.
Tuesday, August 2, 2016
QUIC Best Practice
As
we all know, Google has a habit of updating their code frequently. From a Feature Perspective that is obviously good. From a
Security Perspective this can create a problem. For example, if you have
a DLP Endpoint Agent installed to identify/block confidential posts... you may have issues if Chrome gets too far out in front of your agent. Another example
is QUIC.
https://en.wikipedia.org/wiki/QUIC
This UDP Based Protocol will render your proxies useless as we setup redirection for outbound connections destined to TCP:80 & 443. ESPO Best Practices are as follows:
https://en.wikipedia.org/wiki/QUIC
This UDP Based Protocol will render your proxies useless as we setup redirection for outbound connections destined to TCP:80 & 443. ESPO Best Practices are as follows:
Option 1: Disable Experimental
QUIC protocol on individual Google Chrome browsers. - This can be done by opening Google
Chrome, in the URL type "chrome://flags". Look for Experimental QUIC
protocol and disable it.
Option 2: Block QUIC using firewall
policy - Create a custom firewall service for UDP port 80 and port 443.
Configure a firewall policy with the custom service created and set the action
to Deny. Make sure this policy on top of all (inside/trusted to outside/untrusted)
Option 3: Similar to Option 1, you can utilize a GPO to turn off QUIC protocol. Download the latest chrome adm/admx templates from https://support.google.com/chrome/a/answer/187202?hl=en#windows and find it in Administrative templates > Google Chrome > Allows QUIC protocol. Set to disable.
In summary, the Easy Button answer might be Option 2. Block outbound connections destined to UDP:80 & 443 and the browser will have to fail back to TCP.
Monday, August 1, 2016
New Malware on the Loose
Heads up! The following site is actively hosting malware as of the writing of this Blog Post:
What exactly is the malware doing? Forcepoint indicates nothing good:
Well... I have Cisco you may say... I will be fine: Ummmm no:
OK, Ok, ok... I have a web security solution from 1 of the other 68 solutions available on the market. Oops!
You may then say, I have defense-in-depth... I have a top notch AV solution. Unfortunately, only 2 of 54 AV Engines are actively protecting against this executable:
What can I do to protect against this active threat? Call ESPO Systems for a free consultation.
What exactly is the malware doing? Forcepoint indicates nothing good:
Well... I have Cisco you may say... I will be fine: Ummmm no:
OK, Ok, ok... I have a web security solution from 1 of the other 68 solutions available on the market. Oops!
You may then say, I have defense-in-depth... I have a top notch AV solution. Unfortunately, only 2 of 54 AV Engines are actively protecting against this executable:
What can I do to protect against this active threat? Call ESPO Systems for a free consultation.
Thursday, July 21, 2016
Water-Cooler Talk
When McAfee acquired Secure Computing, we pretty much all suspected Dave DeWalt was putting lipstick on his pig in an attempt to create a liquidity event for himself. You could see a lack of integration and R&D investment from the start... much less an understanding of Network Security. Poor Intel is now stuck holding the goods. Case in point:
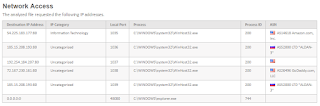
- Current MS Word Document making it's way around the Internet as of 1 hour ago and phoning home to Mother Russia per this Forcepoint Sandbox Report.
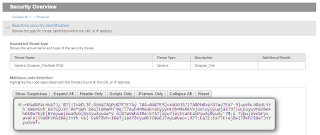
- As you'll note in the above report, the outbound call is detected in real-time by Forcepoint as a generic threat:
- What is the threat? The Forcepoint ACE Engine identifies it as a Dropper File:
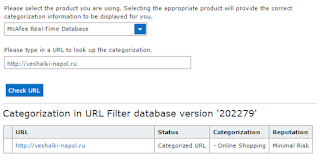
- What does Intel/McAfee think about the site? It's a Shopping site with Minimal Risk from their perspective:
Need help in ripping out your McAfee solution for a true single pane of glass? Connect w/ESPO Systems and request a free consultation.
- Current MS Word Document making it's way around the Internet as of 1 hour ago and phoning home to Mother Russia per this Forcepoint Sandbox Report.
- As you'll note in the above report, the outbound call is detected in real-time by Forcepoint as a generic threat:
- What is the threat? The Forcepoint ACE Engine identifies it as a Dropper File:
- What does Intel/McAfee think about the site? It's a Shopping site with Minimal Risk from their perspective:
Need help in ripping out your McAfee solution for a true single pane of glass? Connect w/ESPO Systems and request a free consultation.
Thursday, July 7, 2016
Own Your Network Security?
Cisco has recently changed their Marketing to correspond with their change of leadership/CEO. Lets test out their current "own your network security" mantra:
1. Microsoft Word documents are propagating across the Internet with malicious macros. If your users have opened it, they would have seen this:
2. If your users enabled editing (the macro), unbeknownst to them, they would have initiated an outbound HTTP connection to this site in Germany:
3. Question - Would Cisco have enabled you to own your security... or been owned? Based on what we see below, it looks like you are owned:
In summary, our work can be double checked via this Forcepoint File Sandbox Report. If you agree with our conclusions, it's likely time to discuss how you can improve your Security Controls. Learn more about our Forcepoint Services here.
1. Microsoft Word documents are propagating across the Internet with malicious macros. If your users have opened it, they would have seen this:
2. If your users enabled editing (the macro), unbeknownst to them, they would have initiated an outbound HTTP connection to this site in Germany:
3. Question - Would Cisco have enabled you to own your security... or been owned? Based on what we see below, it looks like you are owned:
In summary, our work can be double checked via this Forcepoint File Sandbox Report. If you agree with our conclusions, it's likely time to discuss how you can improve your Security Controls. Learn more about our Forcepoint Services here.
Tuesday, June 14, 2016
To Russia with Love
Yes... we know it was "From Russia with Love", however, in this case it's a Post not a Get. Say what? Well... there is a malicious M$ Word document/macro that is on the loose currently. As usual, the AV vendors are asleep at the wheel with only 2 of 57 solutions currently protecting our IT Assets:
Why are we so confident that McAfee and others are wrong? This Forcepoint Sandbox Report proves that rather conclusively.
OK, Ok, ok... why "To Russia..."? Per below, the Dropper file performs an HTTP Post to a WWW site in Mother Russia. This is an obvious outlier as most HTTP/S traffic is Get based rather than Post.
Why would a Post occur rather than a Get? Likely to send out your confidential information. Question - do you have a Data Loss Prevention (DLP) solution monitoring those outbound Posts? What if it was HTTPS vs HTTP? Connect w/ESPO Systems for a free consultation.
Why are we so confident that McAfee and others are wrong? This Forcepoint Sandbox Report proves that rather conclusively.
OK, Ok, ok... why "To Russia..."? Per below, the Dropper file performs an HTTP Post to a WWW site in Mother Russia. This is an obvious outlier as most HTTP/S traffic is Get based rather than Post.
Why would a Post occur rather than a Get? Likely to send out your confidential information. Question - do you have a Data Loss Prevention (DLP) solution monitoring those outbound Posts? What if it was HTTPS vs HTTP? Connect w/ESPO Systems for a free consultation.
Tuesday, May 31, 2016
Macro Malware on the Loose
Heads Up! Another malicious MS Word file is on the loose with a very low detection rate. Forcepoint File Sandbox Report here.
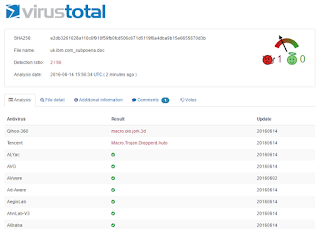
Note that only 3 of 57 Anti Virus Companies are properly detecting this malware:
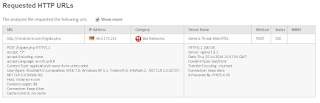
Importantly, per below, note that a number of outbound HTTP Gets occur in which additional malware is downloaded:
Are you safe with old fashion URL Filtering? Ummmm...nope. Per below, this Russian Site is new (Uncategorized). As such, you'll need a sophisticated anti-malware engine on your web proxy, ala Forcepoint's ACE Engine, to stop the 2nd stage of this attack:
Need more info about the Dridex Crew, who's targets have evolved from online banking credentials to this latest round of Locky Ransomware? See the ESPO Systems Multimedia Portal here.
Note that only 3 of 57 Anti Virus Companies are properly detecting this malware:
Importantly, per below, note that a number of outbound HTTP Gets occur in which additional malware is downloaded:
Are you safe with old fashion URL Filtering? Ummmm...nope. Per below, this Russian Site is new (Uncategorized). As such, you'll need a sophisticated anti-malware engine on your web proxy, ala Forcepoint's ACE Engine, to stop the 2nd stage of this attack:
Need more info about the Dridex Crew, who's targets have evolved from online banking credentials to this latest round of Locky Ransomware? See the ESPO Systems Multimedia Portal here.
Wednesday, April 20, 2016
Symantec Misses on Dropper
A malicious Microsoft Word File w/associated macro is making its way across the Internet this morning. How do we know? Our Forcepoint Sandbox detected it... report here.
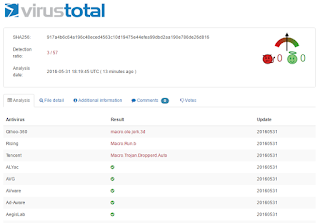
Unfortunately, and as is the case all too often, Symantec is not detecting this malware as proven by VirusTotal:
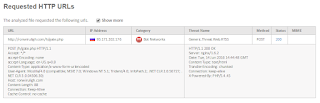
What makes us so certain that this file is indeed malicious? Per below, it's pulling another file down via HTTP:
What does that prove you may ask? Per below, that file is detected as another Dropper by our Forcepoint ACE Engine which is resident on our proxies:
In summary, AntiVirus is a commodity. Do not buy into the pitch that it will solve your security problems. Reduce your security spend on AV and insert Next Gen Security Solutions. Call ESPO Systems for a free consultation/demonstration.
Unfortunately, and as is the case all too often, Symantec is not detecting this malware as proven by VirusTotal:
What makes us so certain that this file is indeed malicious? Per below, it's pulling another file down via HTTP:
What does that prove you may ask? Per below, that file is detected as another Dropper by our Forcepoint ACE Engine which is resident on our proxies:
In summary, AntiVirus is a commodity. Do not buy into the pitch that it will solve your security problems. Reduce your security spend on AV and insert Next Gen Security Solutions. Call ESPO Systems for a free consultation/demonstration.
Tuesday, March 29, 2016
Control-as-a-Service (CaaS)
Anyone tired of hearing that the following architectures solve all the world's problems - SaaS, IaaS, Cloud? Here's a novel concept, why don't we take "control" of our solutions, from a security perspective, and leave our fate in our own hands. Case in point - MedStar Health:
- Per this Computerworld Article, MedStar was attacked over the weekend with the same ransomware that hit the Hollywood Presbyterian Medical Center in mid-February. Per the report, the organization lost "control" of files and their system. Does that sound like a potential HIPAA issue to you?
- Per this earlier ESPO Systems Blog, the Locky Ransomware is leveraging holes in our security controls. To be precise, the malware authors know we dare not block Microsoft Attachments... even if they have malicious macros. They also know AV Signatures are too slow to provide value. As such, the only answer is Sandboxing... ala Forcepoint's Solution.
- So, you likely are asking, what does the MedStar Health Organization use to protect against these threats? Well... they've bought into the Cloud Saves Everything dogma and have given "control" of their security to Google/Postini:
One final question, considering MedStar has given up "control" of their email security, is there much of a chance that outbound email is being monitored for PII or PHI? It may be time to take back control of our security solutions.
- Per this Computerworld Article, MedStar was attacked over the weekend with the same ransomware that hit the Hollywood Presbyterian Medical Center in mid-February. Per the report, the organization lost "control" of files and their system. Does that sound like a potential HIPAA issue to you?
- Per this earlier ESPO Systems Blog, the Locky Ransomware is leveraging holes in our security controls. To be precise, the malware authors know we dare not block Microsoft Attachments... even if they have malicious macros. They also know AV Signatures are too slow to provide value. As such, the only answer is Sandboxing... ala Forcepoint's Solution.
- So, you likely are asking, what does the MedStar Health Organization use to protect against these threats? Well... they've bought into the Cloud Saves Everything dogma and have given "control" of their security to Google/Postini:
One final question, considering MedStar has given up "control" of their email security, is there much of a chance that outbound email is being monitored for PII or PHI? It may be time to take back control of our security solutions.
Thursday, March 3, 2016
Comprehensive Threat Protection?
With the RSA Security Conference coming to a close, we suspect a lot of Security Pros are asking the same questions as us regarding all the dollars thrown at marketing, "really"? That's not to say this intangible expense isn't needed. If the products perform as advertised... we need to get-the-word-out. However, when the marketing is nothing other than an attempt to obfuscate what is happening in the real word, as is the case currently with McAfee, it is our obligation to shed light on this. Case in point:
McAfee is proclaiming to the world that they provide "Comprehensive Threat Protection"
However, as is often the case, malware is currently propagating across the internet via Microsoft Word Documents with Malicious Macros in which McAfee is not providing the protection their Mkting Dept claims. Per below, only 3 of 55 AV Engines currently find a problem with this file:
Need further proof that the file is indeed malicious? Note that files are dropped locally, processes are affected and outbound HTTP calls to Mother Russia are occurring:
In summary, and as is often stated on this blog, AV is a commodity. Improve your security posture by implementing Next Gen Solutions with the cost savings found by reducing your spend on AV.
McAfee is proclaiming to the world that they provide "Comprehensive Threat Protection"
However, as is often the case, malware is currently propagating across the internet via Microsoft Word Documents with Malicious Macros in which McAfee is not providing the protection their Mkting Dept claims. Per below, only 3 of 55 AV Engines currently find a problem with this file:
Need further proof that the file is indeed malicious? Note that files are dropped locally, processes are affected and outbound HTTP calls to Mother Russia are occurring:
In summary, and as is often stated on this blog, AV is a commodity. Improve your security posture by implementing Next Gen Solutions with the cost savings found by reducing your spend on AV.
Friday, February 26, 2016
Malicious Excel File
Around 7:30amCST an Excel Spreadsheet w/macro began propagating across the Internet. If you trust your security to the Anti Virus Vendors, you're likely sipping on a cup of coffee expecting to have an easy day heading into the weekend... as neither McAfee nor Symantec are currently detecting a problem:
However, per this Forcepoint File Sandbox Report, your day is about to change as this file is indeed malicious. Per the report, it attempts to modify 21 Files, 2 Processes and 412 Registry Entries. If that isn't bad enough, this Dropper File will also communicate to sites in Russia and Vietnam to pull down additional malware:
Additionally, if you've entrusted your Web Security to Cisco Ironport and are hoping the phone home to uggs-fashion.ru is blocked... you'll be disappointed. Per below, the site name implies it's a fashion site, and, the Senderbase Reputation System unfortunately agrees:
In summary, security is moving far too fast to rely upon AV Signatures. Contact ESPO Systems for a free consultation regarding how you can protect your IT Assets across the entire Kill Chain.
However, per this Forcepoint File Sandbox Report, your day is about to change as this file is indeed malicious. Per the report, it attempts to modify 21 Files, 2 Processes and 412 Registry Entries. If that isn't bad enough, this Dropper File will also communicate to sites in Russia and Vietnam to pull down additional malware:
Additionally, if you've entrusted your Web Security to Cisco Ironport and are hoping the phone home to uggs-fashion.ru is blocked... you'll be disappointed. Per below, the site name implies it's a fashion site, and, the Senderbase Reputation System unfortunately agrees:
In summary, security is moving far too fast to rely upon AV Signatures. Contact ESPO Systems for a free consultation regarding how you can protect your IT Assets across the entire Kill Chain.
Thursday, February 18, 2016
Locky Ransomware on the Loose
It appears the Dridex Crew has expanded their Cyber Crime Portfolio from the stealing of login credentials to your favorite Financial Institution... to Ransomware. Case in point:
- M$ Word Documents with malicious macros are being distributed via email attachments (sound familiar).
First Question - Will your users allow you to block all inbound Microsoft Word attachments? Likely not...
Second Question - Are your spam prevention techniques 100% effective? Ummm... no.
Third Question - Should we therefore feel confident that your Anti Virus Solution has your back and will detect the file at the gateway or desktop? PLEASE!!!
- Thankfully, the Forcepoint File Sandboxing feature will detect this Ransomware. On the other hand, if you are using an inferior solution, you are likely seeing Help Desk Tickets describe something looking like this:
- Anyone care to know the current AV Detection Rate? Currently only 5 of 54 AV Engines are detecting the file properly. How long do you think it will take before McAfee and Symantec get their act together?
In summary, this is the same crew who took down the Hollywood Presbyterian Medical Center over the weekend. Do you wish to stay out of the news? Need help from an organization who performed over 600 Security Projects in 2015?? Contact ESPO Systems here.
- M$ Word Documents with malicious macros are being distributed via email attachments (sound familiar).
First Question - Will your users allow you to block all inbound Microsoft Word attachments? Likely not...
Second Question - Are your spam prevention techniques 100% effective? Ummm... no.
Third Question - Should we therefore feel confident that your Anti Virus Solution has your back and will detect the file at the gateway or desktop? PLEASE!!!
- Thankfully, the Forcepoint File Sandboxing feature will detect this Ransomware. On the other hand, if you are using an inferior solution, you are likely seeing Help Desk Tickets describe something looking like this:
- Anyone care to know the current AV Detection Rate? Currently only 5 of 54 AV Engines are detecting the file properly. How long do you think it will take before McAfee and Symantec get their act together?
In summary, this is the same crew who took down the Hollywood Presbyterian Medical Center over the weekend. Do you wish to stay out of the news? Need help from an organization who performed over 600 Security Projects in 2015?? Contact ESPO Systems here.
Wednesday, February 10, 2016
AS57389 ZNET-Mikronet Kft
OK... lets follow the bouncing ball again:
1. Microsoft Word doc is being propagated this morning that leverages a naming convention along the lines of "ReportforInvoicexxx.doc". We strongly recommend you block this file from being downloaded as it contains a malicious macro that modifies 24 Files, 2 Processes and 417 Registry Entries. Forcepoint File Sandbox Report here.
2. As is typically the case, the Anti-Virus Vendors are slow in responding as only 5 of 54 companies are accurately detecting the file as malware:
3. So... what does the malware do besides the aforementioned modifications? Per below, it makes an HTTP call outbound to download an additional file:
4. Whats happens when the 65fg67n file is downloaded? Per this Forcepoint File Sandbox Report, the malware author downloads updates from Microsoft (how nice of them to patch our boxes) and additionally phones home to the botnet via TCP Port 843 to a server in Hungary (AS # 57389). Hence the title of our post.
In summary, if you see outbound connections to 87.229.86.20 on your firewall... you have problems. Call ESPO Systems for a free consultation in regards to IT Controls across the entire Kill Chain.
1. Microsoft Word doc is being propagated this morning that leverages a naming convention along the lines of "ReportforInvoicexxx.doc". We strongly recommend you block this file from being downloaded as it contains a malicious macro that modifies 24 Files, 2 Processes and 417 Registry Entries. Forcepoint File Sandbox Report here.
2. As is typically the case, the Anti-Virus Vendors are slow in responding as only 5 of 54 companies are accurately detecting the file as malware:
3. So... what does the malware do besides the aforementioned modifications? Per below, it makes an HTTP call outbound to download an additional file:
4. Whats happens when the 65fg67n file is downloaded? Per this Forcepoint File Sandbox Report, the malware author downloads updates from Microsoft (how nice of them to patch our boxes) and additionally phones home to the botnet via TCP Port 843 to a server in Hungary (AS # 57389). Hence the title of our post.
In summary, if you see outbound connections to 87.229.86.20 on your firewall... you have problems. Call ESPO Systems for a free consultation in regards to IT Controls across the entire Kill Chain.
Tuesday, February 2, 2016
Symantec AWOL Again
Another day, another threat missed by the "Premium" AV/Security companies. Case in point:
- As of 7amCST a Microsoft Word Document w/Malicious Macro began propagating across the internet. Are we sure it's malicious? Yeah... pretty sure:
Forcepoint File Sandbox Report
- As seen above, the malware affects 2 Processes, 24 Files and 418 Registry Entries. If that isn't enough to convince you of it's malicious nature, how about the fact that it also phones home to a known Botnet, and, pulls down an additional executable via HTTP:
- Lastly, if you are hoping your Symantec Security Solution is going to protect you against this Dridex Attack (which is gunning for the login credentials to your bank)... your hope is misplaced as only 4 of 53 AV Companies are currently detecting this threat:
In summary, it's time to reduce your security spend on legacy security solutions (AV) and adopt Next Generation Solutions. Request a free ESPO Systems Consultation here.
- As of 7amCST a Microsoft Word Document w/Malicious Macro began propagating across the internet. Are we sure it's malicious? Yeah... pretty sure:
Forcepoint File Sandbox Report
- As seen above, the malware affects 2 Processes, 24 Files and 418 Registry Entries. If that isn't enough to convince you of it's malicious nature, how about the fact that it also phones home to a known Botnet, and, pulls down an additional executable via HTTP:
- Lastly, if you are hoping your Symantec Security Solution is going to protect you against this Dridex Attack (which is gunning for the login credentials to your bank)... your hope is misplaced as only 4 of 53 AV Companies are currently detecting this threat:
In summary, it's time to reduce your security spend on legacy security solutions (AV) and adopt Next Generation Solutions. Request a free ESPO Systems Consultation here.
Thursday, January 28, 2016
Trust Barracuda?
Yes... we agree that Barracuda is "cost effective". You too could create cost effective solutions if you leveraged open source tools. However, the question needs to be asked, are you willing to reduce your risk posture to save a few bucks? Case in point:
M$ Word file started propagating across the Internet with malicious macros at ~7:45amCST. This file is actually a Dropper File, as shown via this Forcepoint File Sandbox Report, which is attempting to infect your local files and phone home to a website in the US:
What is the Anti-Virus Coverage Rate you may ask for this Dropper File? Not good... only 5 companies currently detect it:
OK... lets assume your security controls have not blocked the download of the dropper, is your Barracuda Solution going to protect you from the download of the actual payload? Ummm... no:
In summary, please contact ESPO Systems if you'd like to implement controls to block the attack across the entire Kill Chain.
M$ Word file started propagating across the Internet with malicious macros at ~7:45amCST. This file is actually a Dropper File, as shown via this Forcepoint File Sandbox Report, which is attempting to infect your local files and phone home to a website in the US:
What is the Anti-Virus Coverage Rate you may ask for this Dropper File? Not good... only 5 companies currently detect it:
OK... lets assume your security controls have not blocked the download of the dropper, is your Barracuda Solution going to protect you from the download of the actual payload? Ummm... no:
In summary, please contact ESPO Systems if you'd like to implement controls to block the attack across the entire Kill Chain.
Wednesday, January 13, 2016
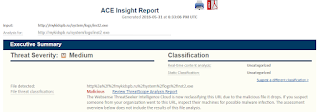
Symantec + Cisco = Bad Day
Do you have Symantec's AV + Cisco's Web Gateway? If so, you may be in for a bad day. Why? Malware is currently working it's way around the Internet that neither vendor is protecting against:
Per this Raytheon|Websense File Sandbox Report, a malicious Word Document is being propagated that is actually a Dropper File for Dridex. If you are hoping Symantec will protect your IT Assets against this threat... you will be disappointed:
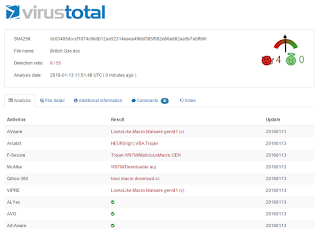
Next, assuming the Dropper File was not detected, it's now downloading additional malware from a website on the GoDaddy domain:
If you are hoping your Cisco / IronPort Web Gateway is protecting your IT Assets... you will be disappointed again:
In summary, your security solution needs to be holistic... you need to have visibility into all 7 steps of the Kill Chain. Call ESPO Systems for a free consultation.
Per this Raytheon|Websense File Sandbox Report, a malicious Word Document is being propagated that is actually a Dropper File for Dridex. If you are hoping Symantec will protect your IT Assets against this threat... you will be disappointed:
Next, assuming the Dropper File was not detected, it's now downloading additional malware from a website on the GoDaddy domain:
If you are hoping your Cisco / IronPort Web Gateway is protecting your IT Assets... you will be disappointed again:
In summary, your security solution needs to be holistic... you need to have visibility into all 7 steps of the Kill Chain. Call ESPO Systems for a free consultation.
Subscribe to:
Comments (Atom)