We know, we know, we know... proxies are complex. It's much easier to install a Next Gen Firewall and check the box. However, what are you going to do about DLP? Additionally, what are you going to do about the latest Cryptolocker attack? Per here and below, Firefoxpatch.exe, which is indeed malware, is being distributed via the phaaccounty-taxes website:
Your answer may be to turn on HTTPS Decryption. We'll let you in on an ugly little secret... most Next Gen Firewalls have performance degradation issues when this feature is turned on per this NSS Labs Test:
Are we saying Next Gen Firewalls are not the answer? Not at all... they are absolutely part of the answer as the IPS, VPN, Application ID capabilities and traditional firewalling features are necessary. However, you need to augment these solutions with feature rich proxies ala the Raytheon|Websense APX Solution to enable a complete Security Architecture. Schedule a briefing with ESPO Systems today to learn more.
Tuesday, December 15, 2015
Thursday, December 10, 2015
Dridex Operational This Morning
A Microsoft Word document, currently named Order Acknowledgement.doc, is propagating across the Internet this morning. Per below, the doc has a malicious macro and is being leveraged as a dropper:
As we've seen all too frequently, the dropper will not only ping the Botnet via high numbered TCP Ports (TCP:3448 today)... but will also pull another exe into the environment:
As stated previously, the FBI was a little too aggressive with it's "marketing" of the takedown of Dridex in mid-October... as this is the same malware variant. And, as has been seen frequently over the last year, our AV Vendors are not keeping up with these initial volleys with only 6 of 55 companies currently detecting:
In summary, the Raytheon|Websense APX Solution is one of the few vendors capable of protecting against this threat... across the entire Kill Chain. Contact ESPO Systems if you'd like to schedule a briefing.
As we've seen all too frequently, the dropper will not only ping the Botnet via high numbered TCP Ports (TCP:3448 today)... but will also pull another exe into the environment:
As stated previously, the FBI was a little too aggressive with it's "marketing" of the takedown of Dridex in mid-October... as this is the same malware variant. And, as has been seen frequently over the last year, our AV Vendors are not keeping up with these initial volleys with only 6 of 55 companies currently detecting:
In summary, the Raytheon|Websense APX Solution is one of the few vendors capable of protecting against this threat... across the entire Kill Chain. Contact ESPO Systems if you'd like to schedule a briefing.
Monday, November 30, 2015
Black Monday
Yes... we know the labels are Black Friday and Cyber Monday. However, a Microsoft Word document with malicious macro is propagating across the Internet this morning (Raytheon|Websense File Sandbox Report here) with only 1 of 54 AntiVirus Engines protecting... hence Black Monday:
Question - with such a poor detection rate by the AV Engines, and, our inability to outright block all incoming Microsoft Files (as our User Communities would scream)... what are you to do? Assuming you're not already protecting yourself with a Raytheon|Websense APX Solution, you may need to scour your firewall logs for the phone home back to the botnet on TCP Port 2448 :-(
Question - with such a poor detection rate by the AV Engines, and, our inability to outright block all incoming Microsoft Files (as our User Communities would scream)... what are you to do? Assuming you're not already protecting yourself with a Raytheon|Websense APX Solution, you may need to scour your firewall logs for the phone home back to the botnet on TCP Port 2448 :-(
Monday, November 23, 2015
Blended Failure
What is a Blended Threat? Per TechTarget, it's one that usually employs multiple attack vectors. In other words, the threat usually comes in via the email threat vector, but, a dropper file typically phones home to pull additional malware via the web threat vector. Today we have an example of the Security Vendors missing on both (other than Raytheon|Websense):
- Word Attachment, with malicious macro, propagating around the internet this morning... details of the Raytheon|Websense File Sandbox Report found here.
- As is usually the case, your trust would be misplaced if you are expecting your AV engines to block this M$ Office Attachment... as only 4 of 55 AV Companies are detecting this:
- Per the above report, and screen shot below, the downloader phones home to a www site in CZ:
- You are likely asking, "would my web security solution block that outbound connection?" Well... only 1 of 66 Web Security Companies are in fact doing that currently:
In summary, your security solution needs to have a presence in both the email & web security spaces (not to mention identification of proprietary data being ex-filtrated). Call ESPO Systems to learn how this can be done in an effective manner.
- Word Attachment, with malicious macro, propagating around the internet this morning... details of the Raytheon|Websense File Sandbox Report found here.
- As is usually the case, your trust would be misplaced if you are expecting your AV engines to block this M$ Office Attachment... as only 4 of 55 AV Companies are detecting this:
- Per the above report, and screen shot below, the downloader phones home to a www site in CZ:
- You are likely asking, "would my web security solution block that outbound connection?" Well... only 1 of 66 Web Security Companies are in fact doing that currently:
In summary, your security solution needs to have a presence in both the email & web security spaces (not to mention identification of proprietary data being ex-filtrated). Call ESPO Systems to learn how this can be done in an effective manner.
Monday, November 16, 2015
Cisco = Detect & Defend?
We see Cisco's new security marketing push; however, that doesn't seem to square with reality currently. Case in point:
- Excel spreadsheet on the loose with a malicious macro. Raytheon|Websense File Sandbox Report here.
- The downloader, per the above report, attempts to pull another exe via HTTP in Finland:
- However, the site in question is currently listed with a "neutral" web reputation. In other words, your users are going there if you are protected by a Cisco IronPort Web Gateway:
In summary, you may ask what the AV Detection Rate for the initial part of the attack (Excel File) is? Not good... only 3 of 54 AV Companies are currently detecting/protecting:
- Excel spreadsheet on the loose with a malicious macro. Raytheon|Websense File Sandbox Report here.
- The downloader, per the above report, attempts to pull another exe via HTTP in Finland:
- However, the site in question is currently listed with a "neutral" web reputation. In other words, your users are going there if you are protected by a Cisco IronPort Web Gateway:
In summary, you may ask what the AV Detection Rate for the initial part of the attack (Excel File) is? Not good... only 3 of 54 AV Companies are currently detecting/protecting:
Tuesday, November 10, 2015
Symantec... how far thou have fallen
An Excel Spreadsheet w/malicious macro (serving as a dropper) is propagating across the Internet this morning. Raytheon|Websense File Sandbox Report found here.
Per the above link, the dropper is pulling an additional executable from Japan (via HTTP) and phoning home on High Numbered TCP Ports to Mother Russia:
Unfortunately, this malware is considered clean by Symantec:
Time to rethink your Security Controls?
Per the above link, the dropper is pulling an additional executable from Japan (via HTTP) and phoning home on High Numbered TCP Ports to Mother Russia:
Unfortunately, this malware is considered clean by Symantec:
Time to rethink your Security Controls?
Thursday, November 5, 2015
O Brothers, Where Art Thou?
Word doc w/malicious macro (Websense File Sandbox Report found here) is on the loose this morning:
Per the above link, the downloader not only pulls another exe from a site in Germany... but also communicates out to a known botnet on a high number port (TCP:6446):
Finally, our Brothers-In-Arms (the AntiVirus guys), are AWOL... not a single engine detects this file currently:
In summary, check your firewall logs for the IPs referenced above. If you see them, remove the PC from the network... your user most likely downloaded the file via email or webmail. Lastly, call us to identify how you can secure those threat vectors better. :-)
Per the above link, the downloader not only pulls another exe from a site in Germany... but also communicates out to a known botnet on a high number port (TCP:6446):
Finally, our Brothers-In-Arms (the AntiVirus guys), are AWOL... not a single engine detects this file currently:
In summary, check your firewall logs for the IPs referenced above. If you see them, remove the PC from the network... your user most likely downloaded the file via email or webmail. Lastly, call us to identify how you can secure those threat vectors better. :-)
Wednesday, October 28, 2015
Anatomy of an "Ongoing" Attack
Emails traversing the internet this morning with malicious Word Attachments:
As usual, AntiVirus coverage is spotty as only 5 of 55 Companies currently have a signature available (McAfee and Symantec are MIA again):
Per this Raytheon|Websense File Sandbox Report, and as is typical with today's Blended Threats, this dropper file pulls another malicious file via HTTP from a site in Germany:
However, something interesting is going on with this 2nd bouncing ball, it phones home to a site in Russia. Of particular interest is the HTTP Post:
Question - are you monitoring outbound HTTP Posts to determine if Intellectual Property or PII is being exfiltrated? Better Question - if the Post was encrypted via HTTPS... would you be able to decrypt it and gain visibility into the data leak?
As usual, AntiVirus coverage is spotty as only 5 of 55 Companies currently have a signature available (McAfee and Symantec are MIA again):
Per this Raytheon|Websense File Sandbox Report, and as is typical with today's Blended Threats, this dropper file pulls another malicious file via HTTP from a site in Germany:
However, something interesting is going on with this 2nd bouncing ball, it phones home to a site in Russia. Of particular interest is the HTTP Post:
Question - are you monitoring outbound HTTP Posts to determine if Intellectual Property or PII is being exfiltrated? Better Question - if the Post was encrypted via HTTPS... would you be able to decrypt it and gain visibility into the data leak?
Wednesday, October 21, 2015
FBI Takes Down Dridex?
Well... that's what the Register reported earlier this month. However, emails are propagating the Internet this morning which smell a lot like Dridex:
Why do we at ESPO Systems believe this to be Dridex? As you see above, the social engineering still revolves around financial concepts and malicious macros are again being leveraged within M$ Office attachments... per this Websense File Sandbox Report.
What's the current AV Detection Rate you ask? Not good:
Why do we at ESPO Systems believe this to be Dridex? As you see above, the social engineering still revolves around financial concepts and malicious macros are again being leveraged within M$ Office attachments... per this Websense File Sandbox Report.
What's the current AV Detection Rate you ask? Not good:
Thursday, October 8, 2015
Pick your Poison
Interesting morning in that both M$ Word and Excel files are being distributed with malicious macros/downloaders that reach out for 983bv3.exe:
- Websense File Sandbox details for Word Downloader found here.
- Websense File Sandbox details for Excel Downloader found here.
As is the case all too frequently, if you're counting on your AV Vendor to protect you, your trust is misplaced:
What's the concern regarding this 983bv3.exe? How about the fact that it will modify 317 Registry Entries... details found here.
In summary, malware is too sophisticated to entrust the AV Vendors with our security. Call ESPO Systems to implement the next generation of Security Controls.
- Websense File Sandbox details for Word Downloader found here.
- Websense File Sandbox details for Excel Downloader found here.
As is the case all too frequently, if you're counting on your AV Vendor to protect you, your trust is misplaced:
What's the concern regarding this 983bv3.exe? How about the fact that it will modify 317 Registry Entries... details found here.
In summary, malware is too sophisticated to entrust the AV Vendors with our security. Call ESPO Systems to implement the next generation of Security Controls.
Thursday, October 1, 2015
Please Open... Not!
Email currently traversing the internet with an M$ Word attachment asking the recipient to "please open". Would your users respond properly?
Per this Websense File Sandbox report, the file is clearly malicious. Unfortunately, the "Premium AV Guys (McAfee & Symantec)" are asleep at the wheel again:
As such, you likely want to check your firewall logs to see if your users did indeed open the attachment/dropper and are therefore phoning home to the following IP Addresses:
Per this Websense File Sandbox report, the file is clearly malicious. Unfortunately, the "Premium AV Guys (McAfee & Symantec)" are asleep at the wheel again:
As such, you likely want to check your firewall logs to see if your users did indeed open the attachment/dropper and are therefore phoning home to the following IP Addresses:
Thursday, September 24, 2015
Blended Threats/Controls
Question - considering the plethora of Blended Threats which leverage both the Email & Web channels to exploit our networks... is it important that our Security Controls have visibility into both mediums?
Case in point - current phishing email traversing the internet which leverages legitimate looking graphics (directly below). Wouldn't it be nice if your web security solution knew of these spam/phishing URLs? On the flip side, wouldn't it be nice if your email security solution knew about malicious URLs?
As you'd expect, the link redirects to a malicious site... located in the Netherlands in this instance. Question - how important is it that your security solutions have a worldwide research team/presence?
Note that the site is attempting to obfuscate the content by leveraging javascript and Base64 encoding:
Final question - wouldn't it be nice if your security solutions not only had a worldwide presence in the Web & Email channels... but could also block active code (javascript, java, active-x) ala the Websense ACE Engine? :-)
Case in point - current phishing email traversing the internet which leverages legitimate looking graphics (directly below). Wouldn't it be nice if your web security solution knew of these spam/phishing URLs? On the flip side, wouldn't it be nice if your email security solution knew about malicious URLs?
As you'd expect, the link redirects to a malicious site... located in the Netherlands in this instance. Question - how important is it that your security solutions have a worldwide research team/presence?
Note that the site is attempting to obfuscate the content by leveraging javascript and Base64 encoding:
Final question - wouldn't it be nice if your security solutions not only had a worldwide presence in the Web & Email channels... but could also block active code (javascript, java, active-x) ala the Websense ACE Engine? :-)
Tuesday, September 15, 2015
Malvertising Campaign
Dark Reading is running a story regarding a 3 week malware campaign in which Online Ad Networks enabled miscreants to redirect clicks to sites hosting the Angler Exploit Kit. The full story can be found here.
Note that the Security Community in general considers this a "big security blunder". However, of special note, is the following quote:
"A fraudulent ad server using HTTPS. We were basically blind to it," he says.
Question - are you still putting off HTTPS Decryption? Wouldn't it be nice if you had Security Controls with visibility into your encrypted traffic and that ongoing attack??
Response - Yes, HTTPS Decryption and proxies in general can be complex... but ESPO Systems can help you with our Best Practices. :-) An additional advantage to consider, as identified within another story running on Dark Reading regarding questionable CAs, found here, is easily addressed when you have a Websense Proxy and thereby have a central location to control CAs:
Note that the Security Community in general considers this a "big security blunder". However, of special note, is the following quote:
"A fraudulent ad server using HTTPS. We were basically blind to it," he says.
Question - are you still putting off HTTPS Decryption? Wouldn't it be nice if you had Security Controls with visibility into your encrypted traffic and that ongoing attack??
Response - Yes, HTTPS Decryption and proxies in general can be complex... but ESPO Systems can help you with our Best Practices. :-) An additional advantage to consider, as identified within another story running on Dark Reading regarding questionable CAs, found here, is easily addressed when you have a Websense Proxy and thereby have a central location to control CAs:
Tuesday, September 1, 2015
Cisco = Security?
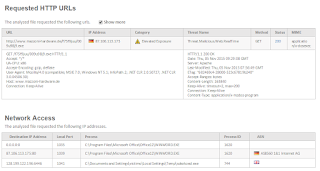
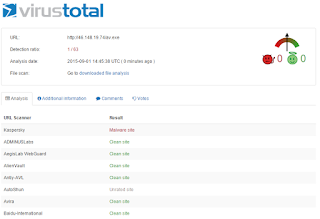
An attack is currently underway in which a dropper file downloads additional malware from the following site:
Per the VirusTotal screenshot below, only 1 of 63 vendors is blocking... other than Websense:
If you've bought into the Cisco dogma of a unified/secure network, you're likely hoping your IronPort Web Proxy with associated SenderBase Reputation System will protect you. Ummmmm... no:
Per the VirusTotal screenshot below, only 1 of 63 vendors is blocking... other than Websense:
If you've bought into the Cisco dogma of a unified/secure network, you're likely hoping your IronPort Web Proxy with associated SenderBase Reputation System will protect you. Ummmmm... no:
Tuesday, August 25, 2015
Another day...
...another attack in which the "Premium" Security Guys (McAfee & Symantec) are AWOL:
- Email traversing the internet this morning with a subject of "Invoice 26949 from I SPI Ltd". The M$ Word attachment is named Report For Inv_26949_from_I__SPI_Ltd_7888.doc
- Per this Websense File Sandbox Report, the malware modifies 23 Files, 2 Processes and 417 Registry Settings. However, the "Premium" Security/AV Guys currently find no problem with the file:
- Additionally, per the above Websense File Sandbox report, you'll notice that the malware also phones home to a site in Poland to download an additional exe. You may therefore ask, "can the "Premium" Security Guys at least protect me from this portion of the blended threat?" Ummm... no:
- Email traversing the internet this morning with a subject of "Invoice 26949 from I SPI Ltd". The M$ Word attachment is named Report For Inv_26949_from_I__SPI_Ltd_7888.doc
- Per this Websense File Sandbox Report, the malware modifies 23 Files, 2 Processes and 417 Registry Settings. However, the "Premium" Security/AV Guys currently find no problem with the file:
- Additionally, per the above Websense File Sandbox report, you'll notice that the malware also phones home to a site in Poland to download an additional exe. You may therefore ask, "can the "Premium" Security Guys at least protect me from this portion of the blended threat?" Ummm... no:
Friday, August 14, 2015
McAfee & Symantec... asleep at the wheel
Remind me again how we block malicious macros in Microsoft Files. Attachment blocking? Nope... not if it's a MS Office file. Antispam signatures? Kinda... but not 100% effective. Antivirus? Well... that's what we've put our trust in for the last decade. Good decision? Consider the following:
- Email traversing the internet this morning with a subject of "invoice" and an attached excel file:
- Per this Websense File Sandbox Report, the file modifies 53 Registry Settings and downloads an executable from a recently compromised site. In fact, the download is from a valid government site for the City of Noale Italy that has recently been compromised. Quick Question/Test - would your web filtering solution block that HTTP connection? :-)
- Lastly, and as is so often the case, the vendors who command such a premium for reactive signature-based AV solutions (McAfee and Symantec) are again MIA. Would it, therefore, make sense to reduce your AV budget by purchasing one of the vendors referenced below, and then reapply those savings towards an advanced security solution?
- Email traversing the internet this morning with a subject of "invoice" and an attached excel file:
- Per this Websense File Sandbox Report, the file modifies 53 Registry Settings and downloads an executable from a recently compromised site. In fact, the download is from a valid government site for the City of Noale Italy that has recently been compromised. Quick Question/Test - would your web filtering solution block that HTTP connection? :-)
- Lastly, and as is so often the case, the vendors who command such a premium for reactive signature-based AV solutions (McAfee and Symantec) are again MIA. Would it, therefore, make sense to reduce your AV budget by purchasing one of the vendors referenced below, and then reapply those savings towards an advanced security solution?
Thursday, August 6, 2015
Symantec Focused on Split?
As Symantec finally realizes that Security + Storage does not equal a valid business model and thereby prepares for their upcoming split, we at ESPO ask a question - is Symantec focused on Wall Street or your security? Consider the following:
- An ~80KB M$ Word doc with malicious macro is traversing the Internet today with a subject line of "Debit". The Websense File Sandbox report can be found here. Note how the malware performs a Zeus-like HTTP POST to a malware site in Germany.
- Convinced it's a bad file that you wouldn't want your Finance Dept receiving? Convinced that your Symantec AV has you covered?? May want to think again regarding that second question:
In closing, it's a nice to see McAfee catching this latest variant as we've beaten up on them recently. However, we still strongly advise clients put a File Sandboxing solution in place ASAP.
- An ~80KB M$ Word doc with malicious macro is traversing the Internet today with a subject line of "Debit". The Websense File Sandbox report can be found here. Note how the malware performs a Zeus-like HTTP POST to a malware site in Germany.
- Convinced it's a bad file that you wouldn't want your Finance Dept receiving? Convinced that your Symantec AV has you covered?? May want to think again regarding that second question:
In closing, it's a nice to see McAfee catching this latest variant as we've beaten up on them recently. However, we still strongly advise clients put a File Sandboxing solution in place ASAP.
Wednesday, July 22, 2015
Magic Quadrant for AV?
No disrespect to the team at Gartner, they are top notch people, but, is there really any value in creating a Magic Quadrant for AntiVirus? The folks at Intel/McAfee were certainly proud of their 7th consecutive year of placement in it, as seen here... even though we've demonstrated their poor catch rate many times in past blog posts. Another example from this morning:
- Emails are traversing the internet this morning with various email subjects that generally refer to international money transfers. Most importantly, a ~160k M$ Word doc is attached that leverages a malicious macro. Details regarding the registry modifications and associated phone home can be found in this Websense File Sandbox Report.
- Importantly, within the report, you will find a link to upload the file to VirusTotal in realtime. Hopefully we will see Symantec and McAfee update their signatures by end-of-business (West Coast Time of course ;-) and detect the file's malicious intent. However, as is all too often the case, you are left to rely upon your antispam sigs/reputation scores (which are 100% accurate right?) to stop these email msgs as the AV vendors are mostly blind to it now:
- Emails are traversing the internet this morning with various email subjects that generally refer to international money transfers. Most importantly, a ~160k M$ Word doc is attached that leverages a malicious macro. Details regarding the registry modifications and associated phone home can be found in this Websense File Sandbox Report.
- Importantly, within the report, you will find a link to upload the file to VirusTotal in realtime. Hopefully we will see Symantec and McAfee update their signatures by end-of-business (West Coast Time of course ;-) and detect the file's malicious intent. However, as is all too often the case, you are left to rely upon your antispam sigs/reputation scores (which are 100% accurate right?) to stop these email msgs as the AV vendors are mostly blind to it now:
Thursday, July 9, 2015
prodasynth.com compromised
This formerly clean site, dedicated to cosmetic sales in France, has been compromised and is now hosting malware:
Redirection to it is primarily driven by a blended threat lure propagating via email, and, unfortunately... only 1 of 63 Web Security Vendors (other than Raytheon|Websense) has detected the compromised site:
Lastly, what type of malware is being hosted you may ask? Well... it's a Dridex Dropper File attempting to steal your banking credentials/money (below). It's therefore slightly important ;-)
Redirection to it is primarily driven by a blended threat lure propagating via email, and, unfortunately... only 1 of 63 Web Security Vendors (other than Raytheon|Websense) has detected the compromised site:
Lastly, what type of malware is being hosted you may ask? Well... it's a Dridex Dropper File attempting to steal your banking credentials/money (below). It's therefore slightly important ;-)
Thursday, June 18, 2015
SouthNorth.Org has Moved
The crew running this recent malware campaign, which ESPO Systems believes to be associated with Dridex, modified their Phone Home Server this week. The campaign began with a malicious macro within M$ Word docs on Monday morning. Per below, AV coverage was weak at that time:
Again, the Raytheon/Websense File Sandbox was able to detonate the file, determine intent and thereby block. However, as you'll see via this link, the phone home is to a server in Germany (136.243.14.142) rather than Russia... although still on TCP Port 8443.
How do we know it's the same crew, well... they're still using the same cert from last week's campaign:
In summary, you may want to create a rule monitoring outbound TCP:8443 looking for the keyphrase of "southnorth.org". Ping us if you need help.
Again, the Raytheon/Websense File Sandbox was able to detonate the file, determine intent and thereby block. However, as you'll see via this link, the phone home is to a server in Germany (136.243.14.142) rather than Russia... although still on TCP Port 8443.
How do we know it's the same crew, well... they're still using the same cert from last week's campaign:
In summary, you may want to create a rule monitoring outbound TCP:8443 looking for the keyphrase of "southnorth.org". Ping us if you need help.
Subscribe to:
Posts (Atom)