1. Microsoft Word file propagating the Internet as of ~8amCDT was detected by our Forcepoint Sandbox:
2. Note the SHA-256 Hash in the above screen shot. Note the same hash below and how only 5 of 53 AV Engines are currently detecting this threat:
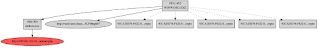
3. How bad is the malware? Per below, it attempts to "post" some of your data to a site in the Ukraine:
In summary, did you see that Freeware AV Engines are detecting this threat? Why is it you're paying all that money to the "enterprise class AV companies"? Again... reduce your spend and invest the savings in next gen solutions. Call ESPO Systems for a free consultation.