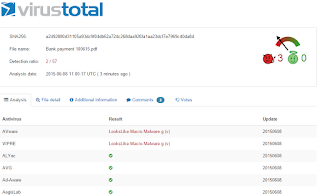
The crew running this recent malware campaign, which ESPO Systems believes to be associated with Dridex, modified their Phone Home Server this week. The campaign began with a malicious macro within M$ Word docs on Monday morning. Per below, AV coverage was weak at that time:
Again, the Raytheon/Websense File Sandbox was able to detonate the file, determine intent and thereby block. However, as you'll see via this link, the phone home is to a server in Germany (136.243.14.142) rather than Russia... although still on TCP Port 8443.
How do we know it's the same crew, well... they're still using the same cert from last week's campaign:
In summary, you may want to create a rule monitoring outbound TCP:8443 looking for the keyphrase of "southnorth.org". Ping us if you need help.
Thursday, June 18, 2015
Thursday, June 11, 2015
SouthNorth.Org in Montana or Russia?
Long story... stick with us. :-)
Blended threat begins with malware delivered via email attachment on Monday morning. As is all too often the case, the AV Vendors were asleep at the wheel (although 29 of 57 AV Engines are detecting at the time of this post):
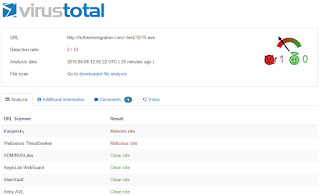
Per this Websense File Sandbox Report, you'll see that the malware downloads an additional exe from lichtermmigration... which only 2 of 63 Web Security Vendors were blocking:
Still with us? Good... because the bouncing ball now takes us to a site in Russia. Per the Websense File Sandbox report referenced above, the malware also phones home to an HTTPS site in Russia, 146.185.128.226. An nmap scan shows something interesting. The svc running on TCP Port 8443 has a cert referencing southnorth.org in Montana:
Hmmm... I guess you really can't trust everything on the Internet. :-)
Blended threat begins with malware delivered via email attachment on Monday morning. As is all too often the case, the AV Vendors were asleep at the wheel (although 29 of 57 AV Engines are detecting at the time of this post):
Per this Websense File Sandbox Report, you'll see that the malware downloads an additional exe from lichtermmigration... which only 2 of 63 Web Security Vendors were blocking:
Still with us? Good... because the bouncing ball now takes us to a site in Russia. Per the Websense File Sandbox report referenced above, the malware also phones home to an HTTPS site in Russia, 146.185.128.226. An nmap scan shows something interesting. The svc running on TCP Port 8443 has a cert referencing southnorth.org in Montana:
Hmmm... I guess you really can't trust everything on the Internet. :-)
Thursday, June 4, 2015
Canary in the Coal Mine
In a recent blog posting, Major Haden, owner of the icanhazip.com domain stated, "You have a problem and icanhazip isn't one of them". That posting was in response to many reports regarding malware calling out to his domain. We agree. Why? An example can be found here.
As you'll see from the above link, the Websense File Sandboxing technology extracted an scr file from a zip, detonated it, and, watched the behavior. As has been all too common of late, the malware performed an HTTP Get to Major's domain. Is that his problem? No. His only problem is that he's created a useful tool to identify source IP Addresses via the cli. Some malware authors now leverage this to determine the geolocation of their victims.
HOWEVER, you can certainly leverage his domain as a "Canary in the Coal Mine". Meaning, if a PC is attempting to connect via TCP:80 to 64.182.208.183... it's likely not for activity related to the generation of revenue. At least not your revenue. :-)
Looking for another Leading Indicator? Check your logs for access to the link shown below (within the image in grey towards the bottom). As you'll see, only 1 of 63 Web Security companies are currently detecting a problem with this site. Then, check out this Websense File Sandbox report from early this morning and you'll see why that is an issue.
As you'll see from the above link, the Websense File Sandboxing technology extracted an scr file from a zip, detonated it, and, watched the behavior. As has been all too common of late, the malware performed an HTTP Get to Major's domain. Is that his problem? No. His only problem is that he's created a useful tool to identify source IP Addresses via the cli. Some malware authors now leverage this to determine the geolocation of their victims.
HOWEVER, you can certainly leverage his domain as a "Canary in the Coal Mine". Meaning, if a PC is attempting to connect via TCP:80 to 64.182.208.183... it's likely not for activity related to the generation of revenue. At least not your revenue. :-)
Looking for another Leading Indicator? Check your logs for access to the link shown below (within the image in grey towards the bottom). As you'll see, only 1 of 63 Web Security companies are currently detecting a problem with this site. Then, check out this Websense File Sandbox report from early this morning and you'll see why that is an issue.
Contact ESPO Systems if you'd like more information on how you can detect and protect your organization against these attacks.
Subscribe to:
Posts (Atom)