Yes... we know the famous James Bond movie was titled, "From Russia with Love", however, in this case we're going to Russia. What? Well.... as previously noted here, the botnet owners are starting to phone home via encrypted channels. We have a similar situation this afternoon with Russia, specifically Moscow, being the destination. Let's follow the bouncing ball:
An M$ Word file is propagating the Internet currently that drops 27 files and launches Powershell:
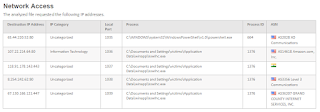
Many connections are initiated outbound, mostly on TCP Port 80, but... notice the TCP:443 connection back to Mother Russia:
How many AV Engines are currently protecting against this threat you ask? Not good... only 7 of 58:
Final question - are you decrypting outbound HTTPS connections? Further, are you interrogating the outbound Posts for DLP Violations? Call ESPO Systems if you need help...
Thursday, August 31, 2017
Monday, July 3, 2017
Phone Home via HTTPS/TCP:443
It's happening! The malware authors are transitioning from HTTP to HTTPS as the callback mechanism to their Botnets. Per this Forcepoint Sandbox Report, you'll see that a Microsoft Word File w/bad macro is propagating today with a very low catch rate... unfortunately only 6 out of 56 Security Companies are currently detecting this as malicious:
Again, per the report above, note how the malware is phoning back home to India via TCP Port 443:
How do we know this server is Command-and-Control for a botnet... via Forcepoint's ThreatSeeker Database:
In summary, this begs a question - are you decrypting your HTTPS traffic? If not, consult with an ESPO Systems expert to discuss Best Practices.
Again, per the report above, note how the malware is phoning back home to India via TCP Port 443:
How do we know this server is Command-and-Control for a botnet... via Forcepoint's ThreatSeeker Database:
In summary, this begs a question - are you decrypting your HTTPS traffic? If not, consult with an ESPO Systems expert to discuss Best Practices.
Tuesday, May 16, 2017
WannaCry Defense
After several days there is still much speculation regarding how this Microsoft Vuln (CVE-2017-0145) is initially being exploited. This is due to the fact that the worm spreads via SMB so aggressively after infestation that it's hard to back track. However, per this report last night, most people are leaning towards inbound emails with attachments.
We at ESPO have been watching the Forcepoint Email Sandbox since Friday and agree. This morning is a perfect example. Emails are coming in with attachments referencing invoices:
As you'd expect, and our endusers unfortunately don't, it's socially engineered to pop open a Word Doc with Macro:
As we follow the bouncing ball you'll note that this blended threat then pulls the actual exploit via the web channel (still in the clear... not using https):
How are the AntiVirus/Next Gen Endpoint guys doing regarding detection rate? Ummm... not good (only 10 out of 57 companies currently detect it):
In summary, ping us at ESPO to discuss how a holistic security solution (Web, Email, Firewall/IPS, Patch Mgt and DLP) can preclude you from wasting time on this latest worm.
We at ESPO have been watching the Forcepoint Email Sandbox since Friday and agree. This morning is a perfect example. Emails are coming in with attachments referencing invoices:
As you'd expect, and our endusers unfortunately don't, it's socially engineered to pop open a Word Doc with Macro:
As we follow the bouncing ball you'll note that this blended threat then pulls the actual exploit via the web channel (still in the clear... not using https):
How are the AntiVirus/Next Gen Endpoint guys doing regarding detection rate? Ummm... not good (only 10 out of 57 companies currently detect it):
In summary, ping us at ESPO to discuss how a holistic security solution (Web, Email, Firewall/IPS, Patch Mgt and DLP) can preclude you from wasting time on this latest worm.
Subscribe to:
Posts (Atom)