Question - considering the plethora of Blended Threats which leverage both the Email & Web channels to exploit our networks... is it important that our Security Controls have visibility into both mediums?
Case in point - current phishing email traversing the internet which leverages legitimate looking graphics (directly below). Wouldn't it be nice if your web security solution knew of these spam/phishing URLs? On the flip side, wouldn't it be nice if your email security solution knew about malicious URLs?
As you'd expect, the link redirects to a malicious site... located in the Netherlands in this instance. Question - how important is it that your security solutions have a worldwide research team/presence?
Note that the site is attempting to obfuscate the content by leveraging javascript and Base64 encoding:
Final question - wouldn't it be nice if your security solutions not only had a worldwide presence in the Web & Email channels... but could also block active code (javascript, java, active-x) ala the Websense ACE Engine? :-)
Thursday, September 24, 2015
Tuesday, September 15, 2015
Malvertising Campaign
Dark Reading is running a story regarding a 3 week malware campaign in which Online Ad Networks enabled miscreants to redirect clicks to sites hosting the Angler Exploit Kit. The full story can be found here.
Note that the Security Community in general considers this a "big security blunder". However, of special note, is the following quote:
"A fraudulent ad server using HTTPS. We were basically blind to it," he says.
Question - are you still putting off HTTPS Decryption? Wouldn't it be nice if you had Security Controls with visibility into your encrypted traffic and that ongoing attack??
Response - Yes, HTTPS Decryption and proxies in general can be complex... but ESPO Systems can help you with our Best Practices. :-) An additional advantage to consider, as identified within another story running on Dark Reading regarding questionable CAs, found here, is easily addressed when you have a Websense Proxy and thereby have a central location to control CAs:
Note that the Security Community in general considers this a "big security blunder". However, of special note, is the following quote:
"A fraudulent ad server using HTTPS. We were basically blind to it," he says.
Question - are you still putting off HTTPS Decryption? Wouldn't it be nice if you had Security Controls with visibility into your encrypted traffic and that ongoing attack??
Response - Yes, HTTPS Decryption and proxies in general can be complex... but ESPO Systems can help you with our Best Practices. :-) An additional advantage to consider, as identified within another story running on Dark Reading regarding questionable CAs, found here, is easily addressed when you have a Websense Proxy and thereby have a central location to control CAs:
Tuesday, September 1, 2015
Cisco = Security?
An attack is currently underway in which a dropper file downloads additional malware from the following site:
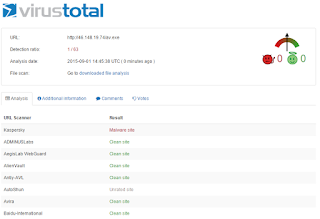
Per the VirusTotal screenshot below, only 1 of 63 vendors is blocking... other than Websense:
If you've bought into the Cisco dogma of a unified/secure network, you're likely hoping your IronPort Web Proxy with associated SenderBase Reputation System will protect you. Ummmmm... no:
Per the VirusTotal screenshot below, only 1 of 63 vendors is blocking... other than Websense:
If you've bought into the Cisco dogma of a unified/secure network, you're likely hoping your IronPort Web Proxy with associated SenderBase Reputation System will protect you. Ummmmm... no:
Subscribe to:
Posts (Atom)