Yes... we know the labels are Black Friday and Cyber Monday. However, a Microsoft Word document with malicious macro is propagating across the Internet this morning (Raytheon|Websense File Sandbox Report here) with only 1 of 54 AntiVirus Engines protecting... hence Black Monday:
Question - with such a poor detection rate by the AV Engines, and, our inability to outright block all incoming Microsoft Files (as our User Communities would scream)... what are you to do? Assuming you're not already protecting yourself with a Raytheon|Websense APX Solution, you may need to scour your firewall logs for the phone home back to the botnet on TCP Port 2448 :-(
Monday, November 30, 2015
Monday, November 23, 2015
Blended Failure
What is a Blended Threat? Per TechTarget, it's one that usually employs multiple attack vectors. In other words, the threat usually comes in via the email threat vector, but, a dropper file typically phones home to pull additional malware via the web threat vector. Today we have an example of the Security Vendors missing on both (other than Raytheon|Websense):
- Word Attachment, with malicious macro, propagating around the internet this morning... details of the Raytheon|Websense File Sandbox Report found here.
- As is usually the case, your trust would be misplaced if you are expecting your AV engines to block this M$ Office Attachment... as only 4 of 55 AV Companies are detecting this:
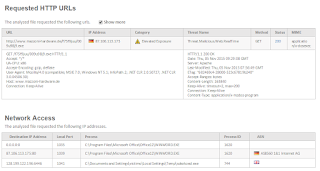
- Per the above report, and screen shot below, the downloader phones home to a www site in CZ:
- You are likely asking, "would my web security solution block that outbound connection?" Well... only 1 of 66 Web Security Companies are in fact doing that currently:
In summary, your security solution needs to have a presence in both the email & web security spaces (not to mention identification of proprietary data being ex-filtrated). Call ESPO Systems to learn how this can be done in an effective manner.
- Word Attachment, with malicious macro, propagating around the internet this morning... details of the Raytheon|Websense File Sandbox Report found here.
- As is usually the case, your trust would be misplaced if you are expecting your AV engines to block this M$ Office Attachment... as only 4 of 55 AV Companies are detecting this:
- Per the above report, and screen shot below, the downloader phones home to a www site in CZ:
- You are likely asking, "would my web security solution block that outbound connection?" Well... only 1 of 66 Web Security Companies are in fact doing that currently:
In summary, your security solution needs to have a presence in both the email & web security spaces (not to mention identification of proprietary data being ex-filtrated). Call ESPO Systems to learn how this can be done in an effective manner.
Monday, November 16, 2015
Cisco = Detect & Defend?
We see Cisco's new security marketing push; however, that doesn't seem to square with reality currently. Case in point:
- Excel spreadsheet on the loose with a malicious macro. Raytheon|Websense File Sandbox Report here.
- The downloader, per the above report, attempts to pull another exe via HTTP in Finland:
- However, the site in question is currently listed with a "neutral" web reputation. In other words, your users are going there if you are protected by a Cisco IronPort Web Gateway:
In summary, you may ask what the AV Detection Rate for the initial part of the attack (Excel File) is? Not good... only 3 of 54 AV Companies are currently detecting/protecting:
- Excel spreadsheet on the loose with a malicious macro. Raytheon|Websense File Sandbox Report here.
- The downloader, per the above report, attempts to pull another exe via HTTP in Finland:
- However, the site in question is currently listed with a "neutral" web reputation. In other words, your users are going there if you are protected by a Cisco IronPort Web Gateway:
In summary, you may ask what the AV Detection Rate for the initial part of the attack (Excel File) is? Not good... only 3 of 54 AV Companies are currently detecting/protecting:
Tuesday, November 10, 2015
Symantec... how far thou have fallen
An Excel Spreadsheet w/malicious macro (serving as a dropper) is propagating across the Internet this morning. Raytheon|Websense File Sandbox Report found here.
Per the above link, the dropper is pulling an additional executable from Japan (via HTTP) and phoning home on High Numbered TCP Ports to Mother Russia:
Unfortunately, this malware is considered clean by Symantec:
Time to rethink your Security Controls?
Per the above link, the dropper is pulling an additional executable from Japan (via HTTP) and phoning home on High Numbered TCP Ports to Mother Russia:
Unfortunately, this malware is considered clean by Symantec:
Time to rethink your Security Controls?
Thursday, November 5, 2015
O Brothers, Where Art Thou?
Word doc w/malicious macro (Websense File Sandbox Report found here) is on the loose this morning:
Per the above link, the downloader not only pulls another exe from a site in Germany... but also communicates out to a known botnet on a high number port (TCP:6446):
Finally, our Brothers-In-Arms (the AntiVirus guys), are AWOL... not a single engine detects this file currently:
In summary, check your firewall logs for the IPs referenced above. If you see them, remove the PC from the network... your user most likely downloaded the file via email or webmail. Lastly, call us to identify how you can secure those threat vectors better. :-)
Per the above link, the downloader not only pulls another exe from a site in Germany... but also communicates out to a known botnet on a high number port (TCP:6446):
Finally, our Brothers-In-Arms (the AntiVirus guys), are AWOL... not a single engine detects this file currently:
In summary, check your firewall logs for the IPs referenced above. If you see them, remove the PC from the network... your user most likely downloaded the file via email or webmail. Lastly, call us to identify how you can secure those threat vectors better. :-)
Subscribe to:
Posts (Atom)