Now that Websense and Raytheon have created a new company that will combine the Intellectual Property (IP) of both entities to create Defense-Grade Cybersecurity, we should all ask, what exactly is that?
One concept that the DoD space leverages, which this new company may bring to the enterprise space, is the Positive Security Model. This concept, when leveraged on firewalls, ensures only known good ports/applications are opened... whereas in the enterprise space we typically allow all 65k TCP Ports outbound and look for negative events. Which model do you think is best equipped to address 0-day threats? :-)
Question #1 - how many of your threats are blended (email & web)? Most I suspect. As such, your users rcv emails that look much like this:
Question #2 - how many of your users are clicking on those links? Again... most I suspect. Wouldn't it be nice if they went to a landing page like this:
Question #3 - wouldn't it be nice if that landing page could leverage sophisticated real-time web security technologies to determine if a threat existed at point-of-click... like this:
How is this a Positive Security Model? It is because we (ESPO Systems) have put our trust in the Websense URL Database. (The industry's most critically acclaimed.) Let us explain: If a URL is unknown/uncategorized by Websense, we've decided to wrap it and send our users to a landing page for real-time inspection. If the website is clean, they are allowed access. In summary, only known good links are allowed into our organization... much like the Positive Security Model only allows known good applications on the firewall.
Wednesday, April 29, 2015
Thursday, April 23, 2015
JSC MediaSoft in Russia Hosting Malware (AS48347)
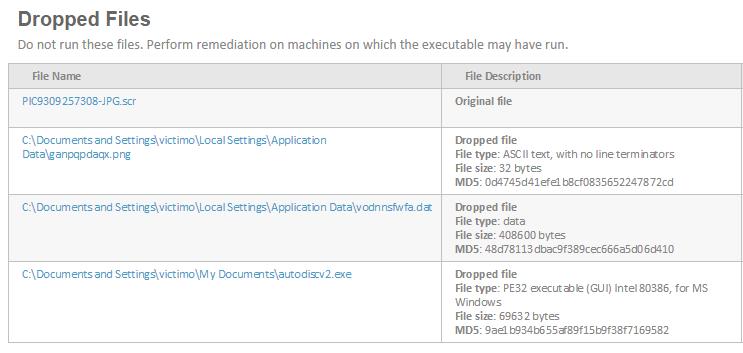
Websense File Sandbox is detecting a downloader being distributed via SCR files within Zips this morning:
As usual, AntiVirus coverage is weak:
As such, you'll want to check your firewall logs for the "phone home" via outbound TCP:80 to Mother Russia:
Question - Do you do business in Russia? Does is make sense to allow HTTP/S Posts to Russia? If not, allow ESPO to align your Business Model with your IT Risk Model.
As usual, AntiVirus coverage is weak:
As such, you'll want to check your firewall logs for the "phone home" via outbound TCP:80 to Mother Russia:
Question - Do you do business in Russia? Does is make sense to allow HTTP/S Posts to Russia? If not, allow ESPO to align your Business Model with your IT Risk Model.
Thursday, April 16, 2015
Jenis_Group Hosting Malware
As of this morning, Websense is identifying malware on this newly compromised site:
Note that the Websense ThreatScope technology has identified malicious intent. So what you ask? Well... would you want an exe delivered via the web channel injecting itself into processes and writing files on your desktops:
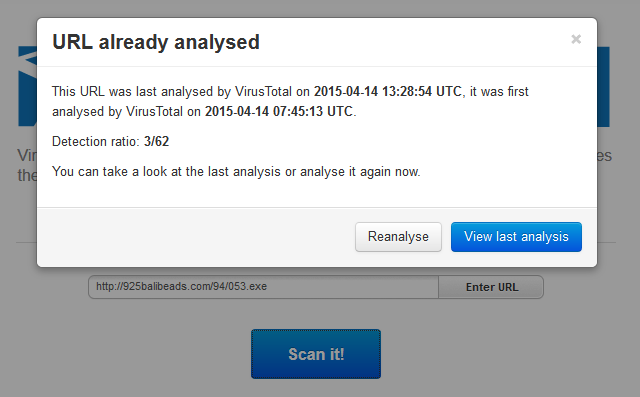
However, and is unfortunately all too frequent, the signature based security vendors are asleep at the wheel with only 1 detection from the 62 AV Engines tested on VirusTotal:
Note that the Websense ThreatScope technology has identified malicious intent. So what you ask? Well... would you want an exe delivered via the web channel injecting itself into processes and writing files on your desktops:
However, and is unfortunately all too frequent, the signature based security vendors are asleep at the wheel with only 1 detection from the 62 AV Engines tested on VirusTotal:
Are you ready yet to contact ESPO Systems about how you can get Websense's Threatscope enabled in your system?
Tuesday, April 14, 2015
Malicious Excel Macro on the Loose
A new malicious Microsoft Excel Macro is making it's way around the internet this morning. Per below, you'll see that the AV Vendors are doing a poor job protecting against this threat... as is all too often the case:
Are we sure that the excel file is malware? As you'll see below, the Websense File Sandbox validates the malicious intent:
Finally, notice that the malware/downloader calls out via HTTP to a new domain. Note that this executable, too, is detected by the Websense ACE Technology:
HOWEVER... note that the AV Vendors are not able to detect this threat either :-(
Are we sure that the excel file is malware? As you'll see below, the Websense File Sandbox validates the malicious intent:
Finally, notice that the malware/downloader calls out via HTTP to a new domain. Note that this executable, too, is detected by the Websense ACE Technology:
HOWEVER... note that the AV Vendors are not able to detect this threat either :-(
Wednesday, April 1, 2015
Really Cisco???
Question - how much is Cisco charging you for the renewal of your IronPort S Class Appliance (web gateway)? And... do you feel the Senderbase Reputation System, and the associated URL Database, is keeping your IT Assets secure? We at ESPO would argue that you consider the following attack emanating out of Hong Kong:
Chinabest-ent.com is leveraging an IP Address currently owned by Network Infinity based out of Hong Kong. If you are a Cisco customer, your users currently have no problem accessing this site as it's currently classified with a Neutral Web Reputation:
However, as proven below, the Websense ACE Technology has identified that the site is hosting malicious content:
More importantly, the malware then attempts to POST data out to a site in Russia:
In summary, we've stated many times how your Security spend could/should be reduced by squeezing your AV Vendors; however, it may be time to redirect your Cisco renewal towards Websense too. :-)
Chinabest-ent.com is leveraging an IP Address currently owned by Network Infinity based out of Hong Kong. If you are a Cisco customer, your users currently have no problem accessing this site as it's currently classified with a Neutral Web Reputation:
However, as proven below, the Websense ACE Technology has identified that the site is hosting malicious content:
More importantly, the malware then attempts to POST data out to a site in Russia:
In summary, we've stated many times how your Security spend could/should be reduced by squeezing your AV Vendors; however, it may be time to redirect your Cisco renewal towards Websense too. :-)
Subscribe to:
Posts (Atom)