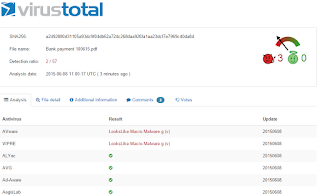
Remind me again how we block malicious macros in Microsoft Files. Attachment blocking? Nope... not if it's a MS Office file. Antispam signatures? Kinda... but not 100% effective. Antivirus? Well... that's what we've put our trust in for the last decade. Good decision? Consider the following:
- Email traversing the internet this morning with a subject of "invoice" and an attached excel file:
- Per this Websense File Sandbox Report, the file modifies 53 Registry Settings and downloads an executable from a recently compromised site. In fact, the download is from a valid government site for the City of Noale Italy that has recently been compromised. Quick Question/Test - would your web filtering solution block that HTTP connection? :-)
- Lastly, and as is so often the case, the vendors who command such a premium for reactive signature-based AV solutions (McAfee and Symantec) are again MIA. Would it, therefore, make sense to reduce your AV budget by purchasing one of the vendors referenced below, and then reapply those savings towards an advanced security solution?
Friday, August 14, 2015
Thursday, August 6, 2015
Symantec Focused on Split?
As Symantec finally realizes that Security + Storage does not equal a valid business model and thereby prepares for their upcoming split, we at ESPO ask a question - is Symantec focused on Wall Street or your security? Consider the following:
- An ~80KB M$ Word doc with malicious macro is traversing the Internet today with a subject line of "Debit". The Websense File Sandbox report can be found here. Note how the malware performs a Zeus-like HTTP POST to a malware site in Germany.
- Convinced it's a bad file that you wouldn't want your Finance Dept receiving? Convinced that your Symantec AV has you covered?? May want to think again regarding that second question:
In closing, it's a nice to see McAfee catching this latest variant as we've beaten up on them recently. However, we still strongly advise clients put a File Sandboxing solution in place ASAP.
- An ~80KB M$ Word doc with malicious macro is traversing the Internet today with a subject line of "Debit". The Websense File Sandbox report can be found here. Note how the malware performs a Zeus-like HTTP POST to a malware site in Germany.
- Convinced it's a bad file that you wouldn't want your Finance Dept receiving? Convinced that your Symantec AV has you covered?? May want to think again regarding that second question:
In closing, it's a nice to see McAfee catching this latest variant as we've beaten up on them recently. However, we still strongly advise clients put a File Sandboxing solution in place ASAP.
Wednesday, July 22, 2015
Magic Quadrant for AV?
No disrespect to the team at Gartner, they are top notch people, but, is there really any value in creating a Magic Quadrant for AntiVirus? The folks at Intel/McAfee were certainly proud of their 7th consecutive year of placement in it, as seen here... even though we've demonstrated their poor catch rate many times in past blog posts. Another example from this morning:
- Emails are traversing the internet this morning with various email subjects that generally refer to international money transfers. Most importantly, a ~160k M$ Word doc is attached that leverages a malicious macro. Details regarding the registry modifications and associated phone home can be found in this Websense File Sandbox Report.
- Importantly, within the report, you will find a link to upload the file to VirusTotal in realtime. Hopefully we will see Symantec and McAfee update their signatures by end-of-business (West Coast Time of course ;-) and detect the file's malicious intent. However, as is all too often the case, you are left to rely upon your antispam sigs/reputation scores (which are 100% accurate right?) to stop these email msgs as the AV vendors are mostly blind to it now:
- Emails are traversing the internet this morning with various email subjects that generally refer to international money transfers. Most importantly, a ~160k M$ Word doc is attached that leverages a malicious macro. Details regarding the registry modifications and associated phone home can be found in this Websense File Sandbox Report.
- Importantly, within the report, you will find a link to upload the file to VirusTotal in realtime. Hopefully we will see Symantec and McAfee update their signatures by end-of-business (West Coast Time of course ;-) and detect the file's malicious intent. However, as is all too often the case, you are left to rely upon your antispam sigs/reputation scores (which are 100% accurate right?) to stop these email msgs as the AV vendors are mostly blind to it now:
Thursday, July 9, 2015
prodasynth.com compromised
This formerly clean site, dedicated to cosmetic sales in France, has been compromised and is now hosting malware:
Redirection to it is primarily driven by a blended threat lure propagating via email, and, unfortunately... only 1 of 63 Web Security Vendors (other than Raytheon|Websense) has detected the compromised site:
Lastly, what type of malware is being hosted you may ask? Well... it's a Dridex Dropper File attempting to steal your banking credentials/money (below). It's therefore slightly important ;-)
Redirection to it is primarily driven by a blended threat lure propagating via email, and, unfortunately... only 1 of 63 Web Security Vendors (other than Raytheon|Websense) has detected the compromised site:
Lastly, what type of malware is being hosted you may ask? Well... it's a Dridex Dropper File attempting to steal your banking credentials/money (below). It's therefore slightly important ;-)
Thursday, June 18, 2015
SouthNorth.Org has Moved
The crew running this recent malware campaign, which ESPO Systems believes to be associated with Dridex, modified their Phone Home Server this week. The campaign began with a malicious macro within M$ Word docs on Monday morning. Per below, AV coverage was weak at that time:
Again, the Raytheon/Websense File Sandbox was able to detonate the file, determine intent and thereby block. However, as you'll see via this link, the phone home is to a server in Germany (136.243.14.142) rather than Russia... although still on TCP Port 8443.
How do we know it's the same crew, well... they're still using the same cert from last week's campaign:
In summary, you may want to create a rule monitoring outbound TCP:8443 looking for the keyphrase of "southnorth.org". Ping us if you need help.
Again, the Raytheon/Websense File Sandbox was able to detonate the file, determine intent and thereby block. However, as you'll see via this link, the phone home is to a server in Germany (136.243.14.142) rather than Russia... although still on TCP Port 8443.
How do we know it's the same crew, well... they're still using the same cert from last week's campaign:
In summary, you may want to create a rule monitoring outbound TCP:8443 looking for the keyphrase of "southnorth.org". Ping us if you need help.
Thursday, June 11, 2015
SouthNorth.Org in Montana or Russia?
Long story... stick with us. :-)
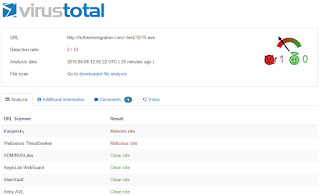
Blended threat begins with malware delivered via email attachment on Monday morning. As is all too often the case, the AV Vendors were asleep at the wheel (although 29 of 57 AV Engines are detecting at the time of this post):
Per this Websense File Sandbox Report, you'll see that the malware downloads an additional exe from lichtermmigration... which only 2 of 63 Web Security Vendors were blocking:
Still with us? Good... because the bouncing ball now takes us to a site in Russia. Per the Websense File Sandbox report referenced above, the malware also phones home to an HTTPS site in Russia, 146.185.128.226. An nmap scan shows something interesting. The svc running on TCP Port 8443 has a cert referencing southnorth.org in Montana:
Hmmm... I guess you really can't trust everything on the Internet. :-)
Blended threat begins with malware delivered via email attachment on Monday morning. As is all too often the case, the AV Vendors were asleep at the wheel (although 29 of 57 AV Engines are detecting at the time of this post):
Per this Websense File Sandbox Report, you'll see that the malware downloads an additional exe from lichtermmigration... which only 2 of 63 Web Security Vendors were blocking:
Still with us? Good... because the bouncing ball now takes us to a site in Russia. Per the Websense File Sandbox report referenced above, the malware also phones home to an HTTPS site in Russia, 146.185.128.226. An nmap scan shows something interesting. The svc running on TCP Port 8443 has a cert referencing southnorth.org in Montana:
Hmmm... I guess you really can't trust everything on the Internet. :-)
Thursday, June 4, 2015
Canary in the Coal Mine
In a recent blog posting, Major Haden, owner of the icanhazip.com domain stated, "You have a problem and icanhazip isn't one of them". That posting was in response to many reports regarding malware calling out to his domain. We agree. Why? An example can be found here.
As you'll see from the above link, the Websense File Sandboxing technology extracted an scr file from a zip, detonated it, and, watched the behavior. As has been all too common of late, the malware performed an HTTP Get to Major's domain. Is that his problem? No. His only problem is that he's created a useful tool to identify source IP Addresses via the cli. Some malware authors now leverage this to determine the geolocation of their victims.
HOWEVER, you can certainly leverage his domain as a "Canary in the Coal Mine". Meaning, if a PC is attempting to connect via TCP:80 to 64.182.208.183... it's likely not for activity related to the generation of revenue. At least not your revenue. :-)
Looking for another Leading Indicator? Check your logs for access to the link shown below (within the image in grey towards the bottom). As you'll see, only 1 of 63 Web Security companies are currently detecting a problem with this site. Then, check out this Websense File Sandbox report from early this morning and you'll see why that is an issue.
As you'll see from the above link, the Websense File Sandboxing technology extracted an scr file from a zip, detonated it, and, watched the behavior. As has been all too common of late, the malware performed an HTTP Get to Major's domain. Is that his problem? No. His only problem is that he's created a useful tool to identify source IP Addresses via the cli. Some malware authors now leverage this to determine the geolocation of their victims.
HOWEVER, you can certainly leverage his domain as a "Canary in the Coal Mine". Meaning, if a PC is attempting to connect via TCP:80 to 64.182.208.183... it's likely not for activity related to the generation of revenue. At least not your revenue. :-)
Looking for another Leading Indicator? Check your logs for access to the link shown below (within the image in grey towards the bottom). As you'll see, only 1 of 63 Web Security companies are currently detecting a problem with this site. Then, check out this Websense File Sandbox report from early this morning and you'll see why that is an issue.
Contact ESPO Systems if you'd like more information on how you can detect and protect your organization against these attacks.
Subscribe to:
Posts (Atom)