As noted previously, the malware authors know that we dare not block inbound Microsoft Office Files for fear of negatively impacting revenue generating processes. To that end, a new attack is underway this morning with malicious macros embedded in a Microsoft Word attachment:
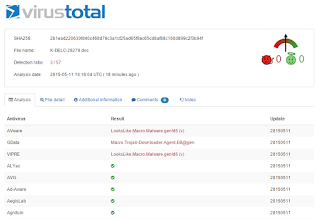
Why would the malware authors send this lure via email attachment... a technique leveraged in the early 2000s? Because they know we trust our AV Vendors to detect malicious intentions. Is that trust misplaced? It would appear so based on the current poor detection rates of this attack:
Is it possible that McAfee & Symantec (not to mention the 52 other companies who missed this) are correct? Is it possible that the Websense APX Solutions we use at ESPO generated a false positive? Check out this report to see for yourself. I suspect the fact that files were dropped on the hard drive, registry entries were re-written, and, a call outbound via HTTP to retrieve an exe will convince you that trust put in AV Companies is trust misplaced.

No comments:
Post a Comment